DEV WALKTHROUGH
- Strider Gearhead
- Feb 19, 2023
- 3 min read
This machine is named as DEV
Firstly we will open the vm and get the ip address.
1. Command: dhclient
2. Ip a
After getting the ip address we will run the nmap scan to know that which ports are open and what services are running on.
Command: nmap -T4 -A <target ip>
Result of nmap scan:

As we can see port 80 is open:

In this bolt document section:

We can see that bolt cms is running, so this could be interesting.
We also saw that port 8080 is also open, so let’s see what’s there:

Now we will do directory fuzzing with the tool named as ffuf.
To install ffuf: sudo apt install ffuf
To do directory fuzzing the commad is: ffuf -w <path/to/wordlist>:FUZZ -u<http://target ip>/FUZZ

We will also do directory fuzzing on port 8080.
Command: : ffuf -w <path/to/wordlist>:FUZZ -u <http://target ip:8080>/FUZZ

We found some directories in port 8080:

dev directory looks interesting, let’s see what’s there:

We can see that here is login page.
We have also saw in the nmap scan that nfs(network file share) was there, So let’s list the directories which are mounted in nsf.
Command: showmount -e <target ip>
-e means export

Here we can see there is a directory /srv/nfs.
So let’s mount that file into our system.
Firstly we will make directory in mnt directory:
Command: mkdir /mnt/dev
Now we will mount the file from target into our system.
Commad: mount -t nfs <target ip:srv/nfs> /mnt/dev/
-t means type

Here we can see that there is a zipped file. So let’s unzip this file.

Here it is asking for the password but we don’t have any password. So let’s bruteforce it. We will use the tool fcrackzip for bruteforcing the password to unzip this file.
Command to install fcrackzip: sudo apt install fcrackzip
Command for using fcrackzip: fcrackzip -v -u -D -p /usr/share/wordlist/rockyou.txt

Here we got the password:

Now we will unzip it.
Command: unzip save.zip

We can see that here are two files.
Todo.txt:

And an id_rsa file. Previously we saw that there was a login page on port 8080 so let’s go there and create an account.
If we will search on google about boltwire exploit so we will found and LFI(Local File Inclusion) exploit

Here we can see that if we use this in the port 8080 url then we can see /etc/passwd.
So lets do this.
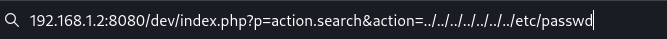

Here we can see a user Jeanpaul so we can login on the behalf of Jeanpaul through ssh coz we also have id_rsa file.
Command: ssh -i id_rsa jeanpaul@<target ip>

Here it is asking for phrase for the key, but we don’t have this right now, so now we will do bruteforce to crack the password for this.
We saw in directory fuzzing on port 80

There are different directory, let’s check all of them manually.
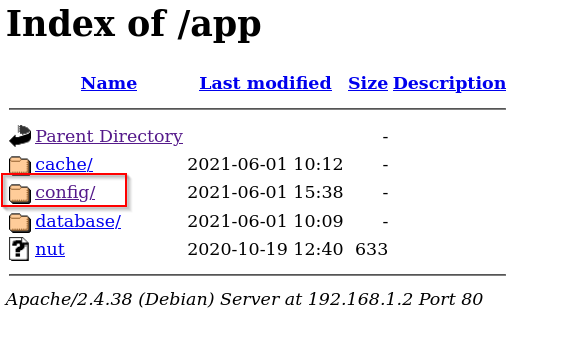
We can see that here is a config file, so let’s explore config file.

Here is an interesting file. Let’s open this file and explore it.

Here we get some credentials, now we will use this password as phrase to login through ssh

We have successfully logged in. So now we have to escalate our privilege as root to get the flag.
Now if we will check the commands we can run as sudo,
Command: sudo -l

Here we can see that we can run zip as sudo. Now we will go to gtfobins to check the command for zip as sudo to get root access.

We can use this command to get root access.
Command: TF=$(mktemp -u)
sudo zip $TF /etc/hosts -T -TT 'sh #'
Now we have gained the root access.
And here is the flag.

CONGRATULATIONS YOU HAVE SOLVED THIS MACHINE AND IF YOU LIKE THIS WRITEUP KINDLY LET ME KNOW IN THE COMMENT.



Comments