Butler Walkthrough
- Strider Gearhead
- Feb 22, 2023
- 2 min read
Butler is a windows based machine.
Link to download the machine for VMware: https://drive.google.com/file/d/199WRUNVP5QAl88fvq74hI_z4P3CTU5PM/view?usp=share_link
For virtual box: https://drive.google.com/file/d/1HgYD9JLl480hlpWSVQyN7doMx1wFnkg_/view?usp=share_link
Link to My medium: https://medium.com/@stridergearhead
So as always our first step is to run the nmap scan.
Command: nmap -T4 -p- -A <target ip>

Result of the nmap scan:

Here we can see many ports are open, but at port 8080, there is a webpage, So let’s checkout:

Here is a Login page but we don’t have any password,
So we have to brute force to get the login id and passwords.
We will use Burp suite for this attack.
Let’s first set foxy proxy to use Burp suite.
Go to google and search for foxy proxy extension and install it, and do this settings in your foxy proxy:

Click save an on the proxy from extensions.
Now open burpsuite and turn on the intercept in the proxy section:

Now go to browser and enter any username and password,
The go to your burp suite and you will see the request:

By right click, sent it to repeater and intruder.
Now go to intruder and by selecting the username click on add:

Do this adding one by one, Now select attack type as cluster bomb.
Now Go to payloads and select 1 and add usernames one by one:
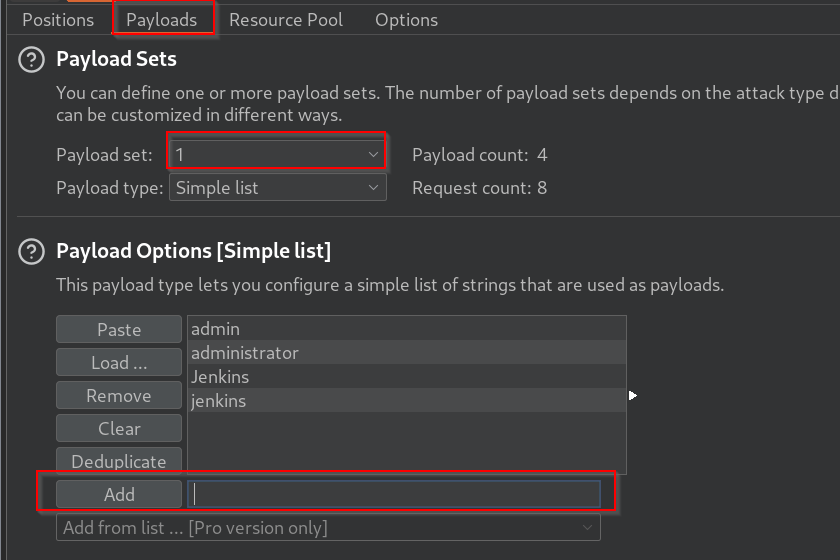
Now select 2 and add some bad passwords:

Now click on start attack, Notice the length:

We got the id and password, Let’s login through these credentials.
Now we have successfully logged in:

Now we have to explore this login page for some vulnerability. And exploring this website we found a Script Console:

It is in the manage Jenkins sections, Let’s see what type of script we can run inside this to get the reverse shell.

Here we can see that we can run Groovy script Inside this, so let’s google for a reverse shell groovy script.

Here we have to put our ip address, let’s setup a listener to catch the reverse shell.
Command: nc -nlvp 8044

Now we will run that script.

And here we are………..
We are butler now on this machine,
You can escalate privilege using winpeas.
IF YOU WANT ME TO MAKE THE WRITEUP FOR PRIVILEGE ESCALATION THEN LET ME KNOW IN THE COMMENT OR YOU CAN DM ME ON INSTAGRAM….



Comments